
Over the last several years, the use of smart wearables continued to grow despite slowing sales. Among the many models, the Apple Watch Series 3 occupies a special spot. Introduced back in 2017, this model is still available new, occupying the niche of the most affordable wearable device in the Apple ecosystem. All that makes the Series 3 one of the most common Apple Watch models. The latest update to iOS Forensic Toolkit enables low-level extraction of the Apple Watch 3 using the checkm8 exploit.
Usage increase despite slowing sales
The sales of smart watch devices have fallen sharply in 2021 due to the economic recession. About 138 million units of smart wearables have been sold in 2021 compared to some 336.5 million shipped in 2019. Despite slowing sales, the use of smart wearables has been steadily increasing, with Apple holding the biggest share of the market: Apple Watch models accounted for some 28.8% of all smart wearable devices sold in 2021.
At the lower end of these models sits the humble Apple Watch Series 3. Priced at $199, this model is the most affordable Apple Watch device currently available from Apple. While Apple does not reveal the details on how many units of each generation watch they sold, the Series 3 have been the Apple Watch model available on the market since 2017, which makes it the longest-available Apple Watch model.
The S3 SoC bootloader vulnerability and checkm8
The Apple Watch 3 was released together with the iPhone 8/iPhone X generation of devices; it is built using the Apple S3 SoC, which roughly corresponds to the SoC architecture Apple used to make the A10 or A11 chips (reportedly closer to the former). The SoC used in the Series 3 has the same bootloader vulnerability as the iPhone SoC and is susceptible to the checkm8 exploit. This in turn opens the door to forensically sound low-level extractions.
While fully patching the exploit would not be possible due to the nature of the vulnerability, for some iPhone models (the iPhone 7, 8 and iPhone X generations) Apple attempted to mitigate it somewhat by changing the boot order and data unlock in iOS 14. For this reason, one must remove the screen lock passcode from iPhone 7/8/X devices when applying the checkm8 exploit. Interestingly, watchOS 8 (which corresponds to iOS 15) did not receive the same treatment, leaving the vulnerability unpatched. This means that the checkm8 exploit can be applied to the Series 3 without removing the passcode from the watch (naturally, the passcode still must be known).
Apple Watch appearances in crime scenes
Smart wearable devices frequently appear in crime scenes. The Apple Watch and the data they collect helped solve numerous cases and helped in many criminal investigations. Some recent examples include:
- Smartphone and smartwatch data led to murder confession – 9to5Mac
- Khashoggi Apple Watch recording in Saudi Consulate nearly impossible (cnbc.com)
- Apple Watch Health Data Is Being Used as Evidence in an Australian Murder Trial (gizmodo.com)
- How an Apple Watch Could Decide a Murder Case | by Thomas McMullan | Medium
“Smartphone and smartwatch data provided crucial evidence that led yesterday to a man confessing to murdering his wife. The data showed that his story about what happened could not have been true…” So what kinds of data, exactly, have helped investigators solve these cases? It’s mostly about the users’ activities:
[…] Caroline Crouch’s biometric watch revealed her pulse readings on the day she died. Babis Anagnostopoulos’s movements were also tracked via his mobile phone, and the couple’s surveillance system also highlighted discrepancies […]
Caroline Crouch’s smart watch showed that her heart was still beating at the time her husband claimed she was murdered. The activity tracker on his phone showed him moving around the house while he said he was tied up […]
In Apple’s ecosystem, the movements (steps, stair flights etc.) and biometric activities (pulse readings etc.) are collected through the HealthKit API and stored in the Apple Health app both on the device and, if enabled, in iCloud. When stored in the cloud, Health data is end-to-end encrypted; it’s not accessible even to Apple and it is not provided by Apple to the law enforcement when the company serves government requests.
Elcomsoft is the only company on the market to obtain and decrypt end-to-end encrypted Health data from Apple iCloud. Our company was also the first on the market to perform logical extraction of the Apple Watch using commercially available adapters. Logical extraction of the Apple Watch returns very little data. While the data includes media files with metadata, the list of installed apps and some diagnostic logs, the data available via logical acquisition does not deliver any information about the user’s physical activities and their biometric conditions. Extracting pulse readings or detecting the user’s movements on the day of the crime would not be possible via logical acquisition if the watch was the only source of evidence.
Low-level analysis helps solve the issue by extracting everything available in the watch. In checkm8 Extraction of Apple Watch Series 3 we discussed the acquisition steps; but what about the analysis?
Apple Watch forensics is still at its infancy. Back in 2019 our colleague Mattia Epifani published an article Apple Watch Forensics 02: Analysis. Since then, not a lot of research was done on how to extract or analyze data obtained from Apple Watch devices, which made us do our own research.
Apple Watch extraction methods
There are several extraction methods available to access some of the data collected by the Apple Watch. These include:
- Cloud extraction, specifically the Health app. Elcomsoft Phone Breaker is the only tool on the market that can extract end-to-end encrypted Health data.
- Logical acquisition: only returns a very limited set of data (media files with metadata, diagnostic logs, list of installed apps).
- Backups: watchOS does not have an externally accessible backup service. However, watch backups (with very limited set of data) are created periodically and stored in the file system of the paired iPhone. One may be able to extract such backups when acquiring the paired iPhone.
- Direct extraction: the most comprehensive method yet. Available for Apple Watch 3; potentially also available for Apple Watch 2.
What about other models?
- Apple Watch S2: the checkm8 exploit is applicable, and the watch can be potentially supported with iOS Forensic Toolkit. However, due to the age of this model, support will be only added on request.
- Apple Watch S4 through S6 (including Watch SE): at this time, logical extraction only. The checkm8 exploit is no longer applicable.
- Apple Watch S7: this model does not have a physical connector; no USB adapters can be made.
Apple Watch 3 file system and keychain analysis
The low-level extraction of the Apple Watch returns significantly more information compared to the logical extraction. The extracted data includes an image of the watch file system (a TAR archive) and a copy of the keychain containing the user’s passwords. Analyzing the file system helps gain access, among other things, to the following types of data:
- Comprehensive Health data
- Comprehensive location history
- System events: network usage, app activity, watch unlocks, contact access, Bluetooth events etc.
- Call logs
- Messages: SMS and iMessage
- Contacts
- Wallet (tickets, boarding passes, discount cards etc.)
- And, of course, the keychain
Let’s start with the keychain. In iOS and macOS, the keychain securely stores the user’s authentication credentials such as their logins, passwords, keys, and two-factor authentication secrets. watchOS holds a copy of the keychain synchronized via iCloud Keychain. You can access that data by opening the extracted keychain file in Elcomsoft Phone Breaker:
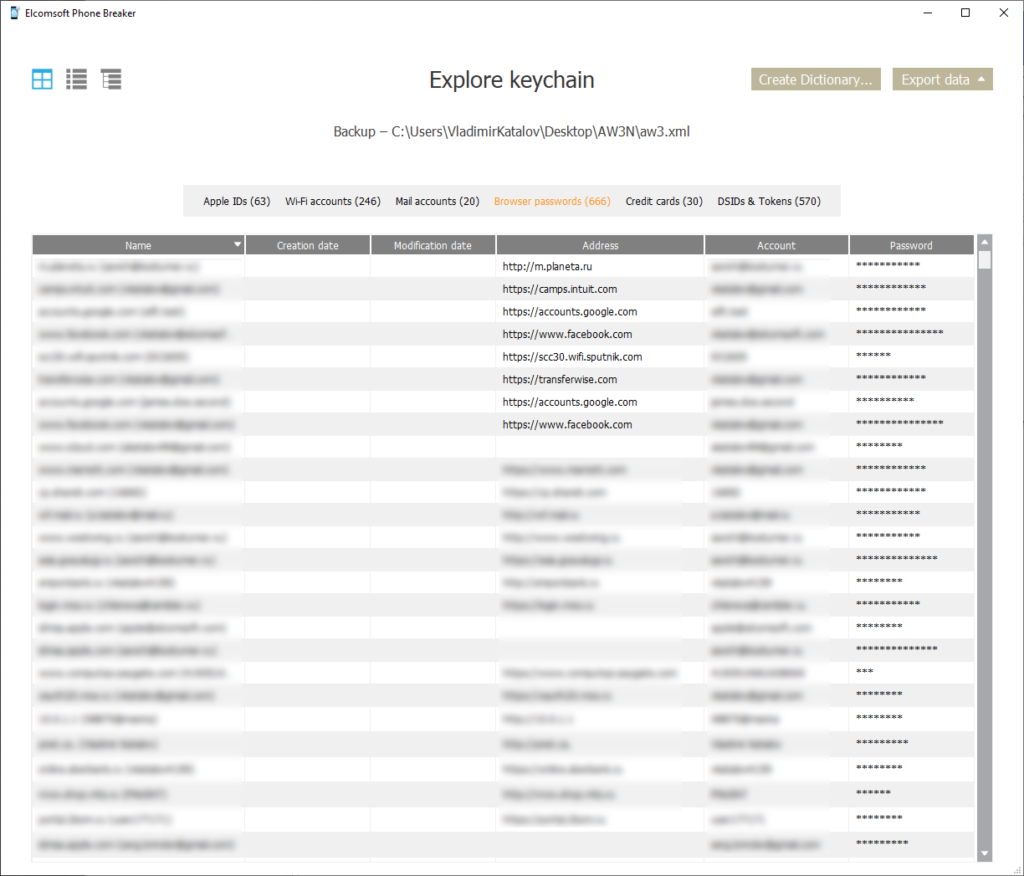
Apple Watch also stores location data, lots of which is synchronized from other devices via iCloud. You can use Elcomsoft Phone Viewer to access location information:


One of the most important types of data stored in the Apple Watch is Health data, which contains biometric measurements performed by the Watch built-in sensors. The Health data includes heart rate, sleep tracking data, step counts (walking data with timings), and workouts.
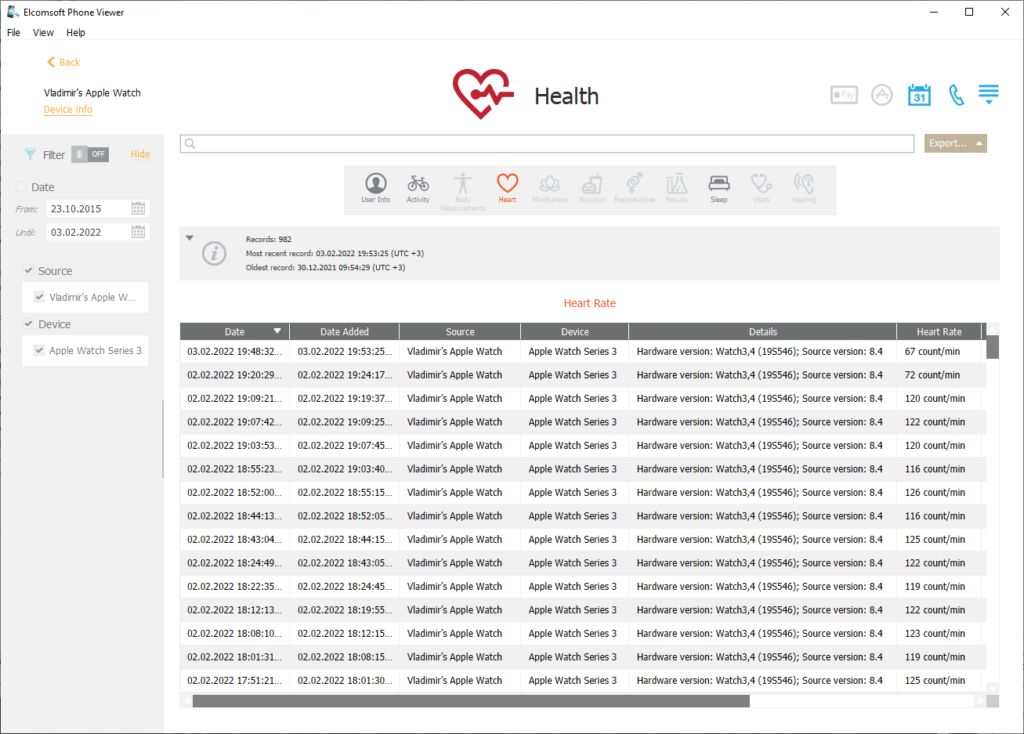
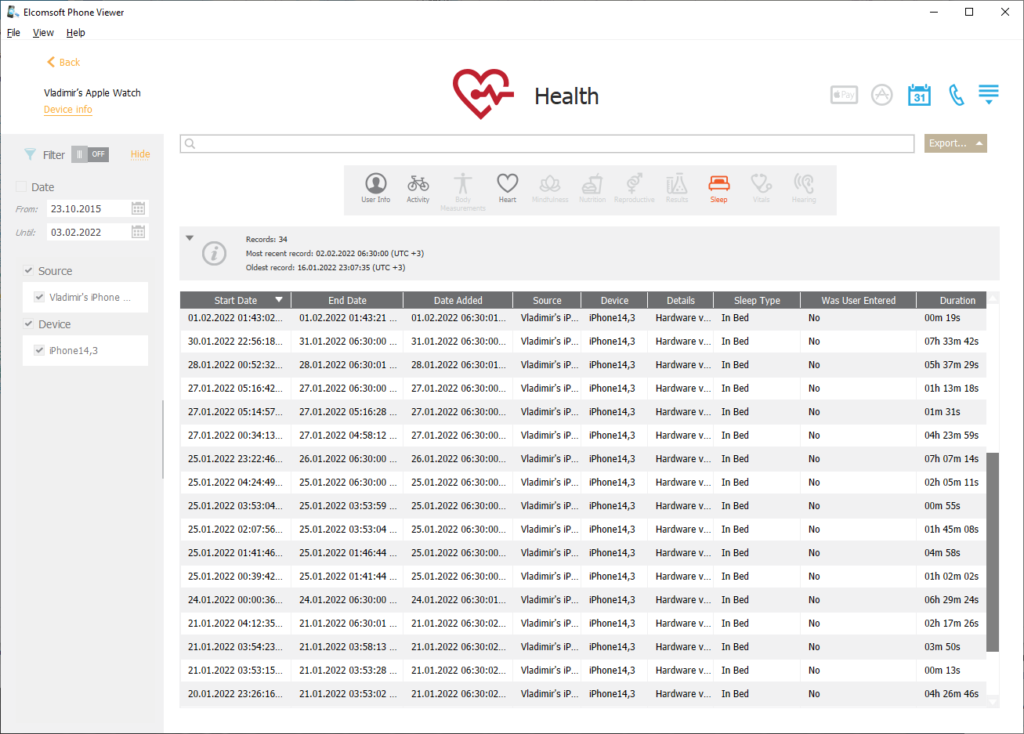

The workouts are one of the more interesting types of data. watchOS has automatic workout detection. Once the watch detects the type of physical activity it recognizes as a workout, it starts monitoring and recording the user’s biometric parameters (e.g. heart rate), steps, as well as collecting precise location data. Analyzing automatically detected workouts can help experts in their investigations.

Third-party tools
You can also use third-party tools such as Oxygen Forensic Detective to analyze the Apple Watch tarball (the file system image in TAR format).
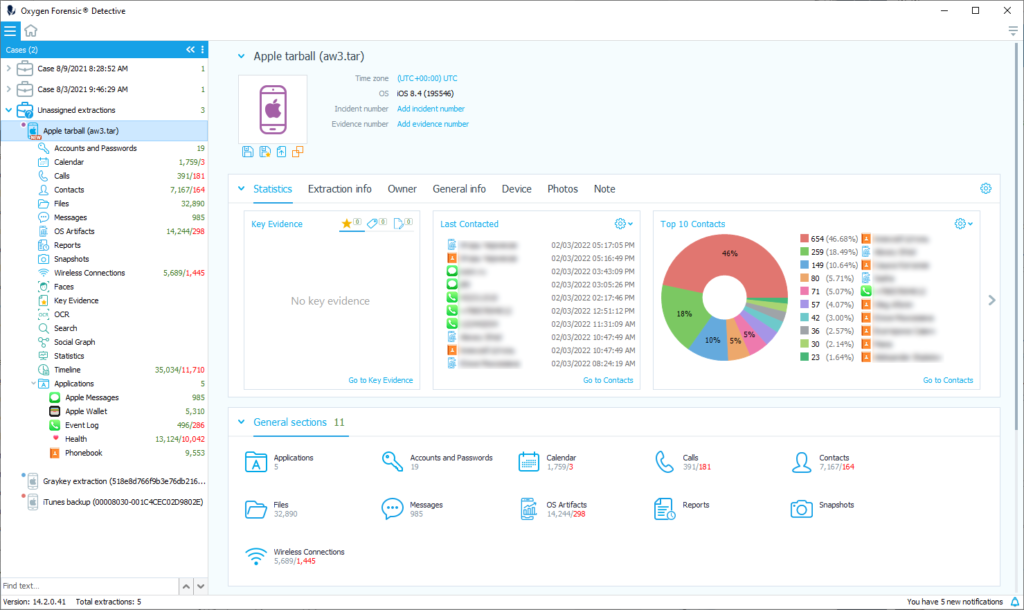
Conclusion
Wearable device forensics is still at its infancy. Few dedicated tools are available to process watch-specific artifacts, with most existing solutions relying on the same analysis techniques they apply to analyze iOS file system images. The ability to extract the file system from the Apple Watch 3 will help developers better understand the specifics of the Apple Watch file system and the differences between iOS and watchOS file system images.