The unc0ver v5 jailbreak has been available for a while now. It supports the newest versions of iOS up to and including iOS 13.5, and this is fantastic news for DFIR community, as it allows extracting the full file system and the keychain when acquiring the newest latest iPhone models such as the iPhone 11 and 11 Pro, and SE 2020. In this article, I’ll talk about the unc0ver jailbreak, the installation and usage for the purpose of file system extraction, and discuss the differences between jailbreak-based and jailbreak-free extraction.
Introduction
As you may know, Elcomsoft iOS Forensic Toolkit supports several different acquisition methods, all with their pros and contras. Let’s go through them briefly.
Logical acquisition
Logical acquisition is 100% compatible with all device models and versions of iOS. it is very simple and effective to use, and sometimes allows obtaining the data even from locked devices with an unknown passcode. Compared to other methods, logical returns a limited amount of data (both from the file system and the keychain).
Full file system and keychain acquisition (with jailbreak)
At this time, jailbreaks are available for most devices and versions of iOS. Once installed, a jailbreak generally allows accessing all the data. However, this method is not forensically sound (as make significant changes to the device), and a bit risky.
Full file system and keychain acquisition (without a jailbreak), agent-based
Probably the best method, when applicable. Jailbreak-free extraction is absolutely safe, and allows to get the same amount of data as with a jailbreak. Note that you will need an Apple Developer Account (but it is worth to have it anyway).
We recommend using agent-based extraction, where applicable and available. Currently, we support agent-based extraction for all devices running iOS 11.0 to 13.4.1 (note that for iOS 13.3.1-13.4.1 there is no keychain extraction but only file system acquisition, see Full File System Extraction for iOS 13.3.1, 13.4 and 13.4.1 for more information).
For the iPhone 5s through iPhone X, you can alternatively install the checkra1n jailbreak (supporting iOS 12.3 to 13.5); the benefit of which is the ability to perform BFU (Before First Unlock) acquisition of locked and disabled devices.
The new unc0ver jailbreak
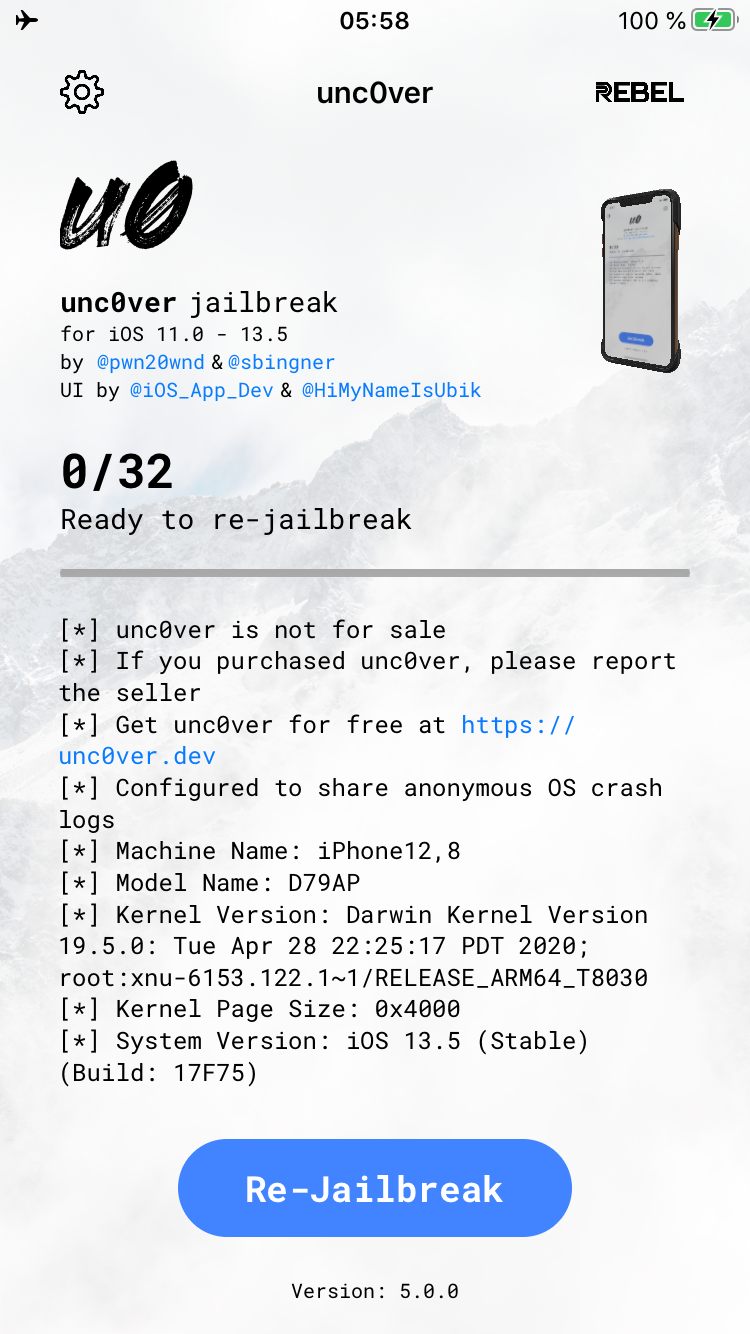
So what is the deal about unc0ver v5? It has added iOS 13.5 support for all the devices from iPhone 6s to iPhone 11 and SE 2020.
We tested the new jailbreak in mere hours after it was released. We have over 50 devices in our lab, running iOS versions ranging from iOS 3.0 to 13.5, but it was enough to try just the three latest ones. We tested one iPhone 6s (based on Apple A9 SoC), one iPad Pro 3rd gen (Apple A12), and one iPhone SE 2020 (Apple A13, the latest one).
Jailbreak installation has never been easier: just sideload the jailbreak IPA file using Cydia Impactor and an Apple developer account (recommended). You can also install the jailbreak via the AltStore, as described on the unc0ver support page, but it has its share of risks. Then you click on the unc0ver icon, and basically that’s it. Make sure to check the “(Re)Install OpenSSH” option before jailbreaking; after device reboots for the first time and before running unc0ver one more time (that’s how the jailbreak works), you will have to do that again.
That’s it, you can use iOS Forensic Toolkit now to perform full file system acquisition. Do not forget to run the (D)isable lock command first, or simply set Auto-Lock: Never in the device settings if you are allowed to, to prevent locking the screen during acquisition. If the screen locks, some of the file cannot be copied.
The keychain
With the new unc0ver jailbreak, you can currently perform keychain acquisition from iOS 13.3.1-13.4.1 devices. Make sure to understand and weigh the risks and forensic consequences. On these versions of iOS, agent-based extraction delivers safety but limited amount of data (file system only), while jailbreaking returns both the file system and the keychain if you can afford some risks.
As for iOS 13.5, the extraction of the keychain is not available at the moment (with either unc0ver or checkra1n). Looks like Apple has made some security improvements related to the keychain, and the old trick does not work anymore. Still, we will do our best to implement keychain extraction for iOS 13.5!
Conclusion
Cat and mouse game goes on! Apple is continuously improving security in their products, from iOS to iCloud, security researches are looking for new vulnerabilities, and forensic vendors keep tracking them and update their products to make forensic experts job more effective.