We have recently updated Elcomsoft iOS Forensic Toolkit, adding the ability to acquire the file system from a wide range of iOS devices. The supported devices include models ranging from the iPhone 5s through the iPhone X regardless of the iOS version; more on that in iOS Device Acquisition with checkra1n Jailbreak. In today’s update (for both Windows and macOS platforms as usual), we’ve added the ability to extract select keychain records in the BFU (Before First Unlock) mode. We have a few other changes and some tips on extracting locked and disabled devices.
BFU Forensics
The BFU stands for “Before First Unlock”. BFU devices are those that have been powered off or rebooted and have never been subsequently unlocked, not even once, by entering the correct screen lock passcode.
In Apple’s world, the content of the iPhone remains securely encrypted until the moment the user taps in their screen lock passcode. The screen lock passcode is absolutely required to generate the encryption key, which in turn is absolutely required to decrypt the iPhone’s file system. In other words, almost everything inside the iPhone remains encrypted until the user unlocks it with their passcode after the phone starts up.
It is the “almost” part of the “everything” that we target in this update. We’ve discovered that certain bits and pieces are available in iOS devices even before the first unlock. In particular, some keychain items containing authentication credentials for email accounts and a number of authentication tokens are available before first unlock. This is by design; these bits and pieces are needed to allow the iPhone to start up correctly before the user punches in the passcode.
Imaging Locked and Disabled Devices
First, the disclosure. We cannot and will not help unlocking iOS devices. We are offering other possibilities not requiring the unlocking. It is often possible to perform the full logical acquisition, extracting the backup, media files and logs, with the help of lockdown/pairing records. The more interesting option is available for select Apple devices that have a bootrom vulnerability exploited by the developers of the checkra1n jailbreak. For these devices (iPhone models ranging from the iPhone 5s through the iPhone X) we can perform a partial file system extraction even if the screen lock passcode is not known.
With Elcomsoft iOS Forensic Toolkit, you can now extract the keychain as well. Yes, in BFU mode, even if the device is locked or disabled (“Connect to iTunes”). While this is only a partial keychain extraction, as most keychain records are encrypted using the key derived from the user’s passcode, this is much better than nothing – and coming from a locked device!
What about disabled devices, when an incorrect passcode has been entered 10 times in a row, and the device prompts you to connect to iTunes (where you can only completely reset the device)? Unless the Erase data option is enabled, the data is still there; it’s just not available for extraction via regular means. BFU acquisition still works even in this case, and you can even extract parts of the keychain.
BFU Keychain Extraction
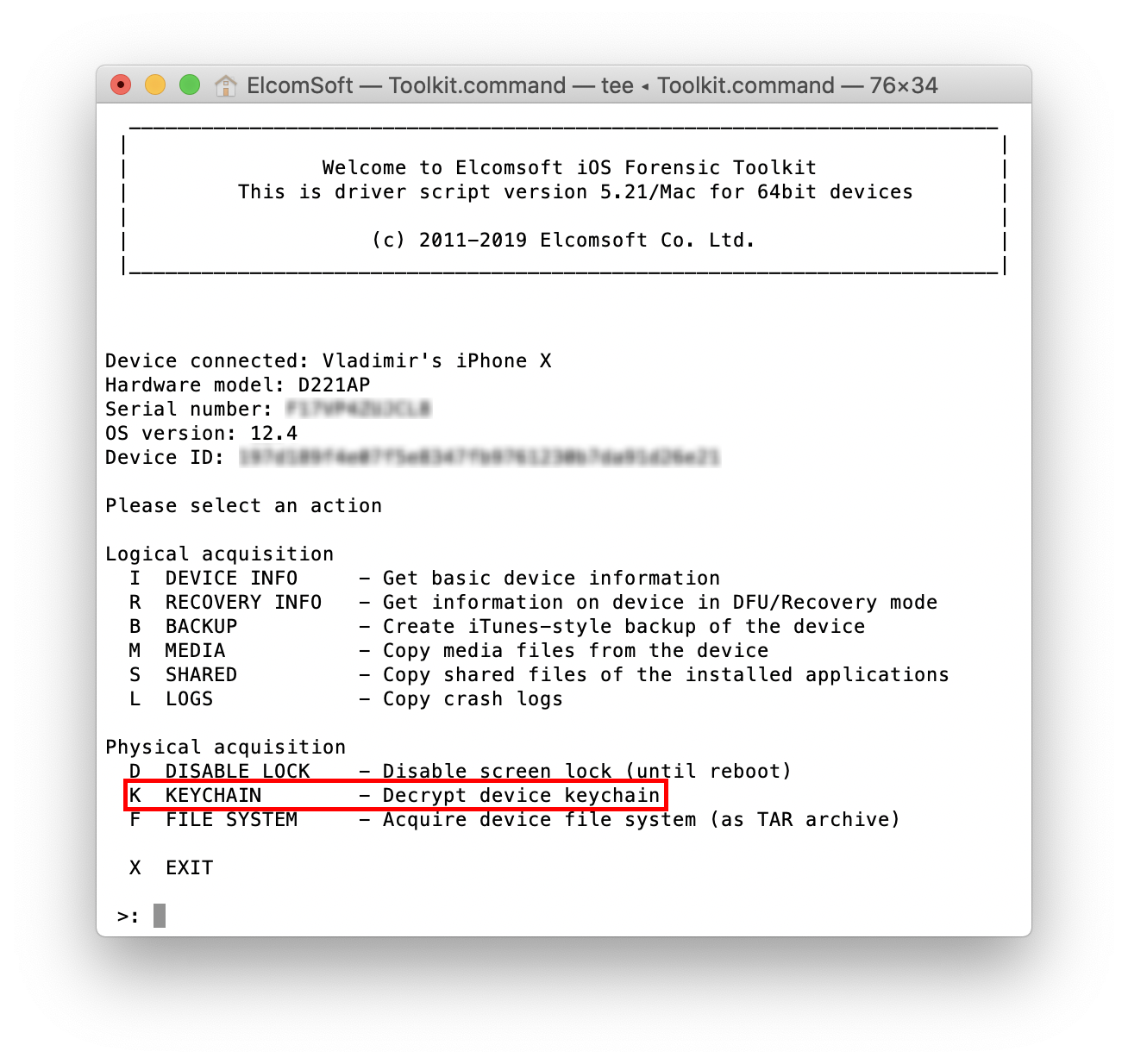
The ([K]eychain) option now works even in the BFU (Before First Unlock) mode. In the AFU (After First Unlock) mode, you had to enter the device passcode in order to unlock the keychain. As the passcode is not known (otherwise you would perform AFU acquisition instead), simply skip this step by pressing Enter:
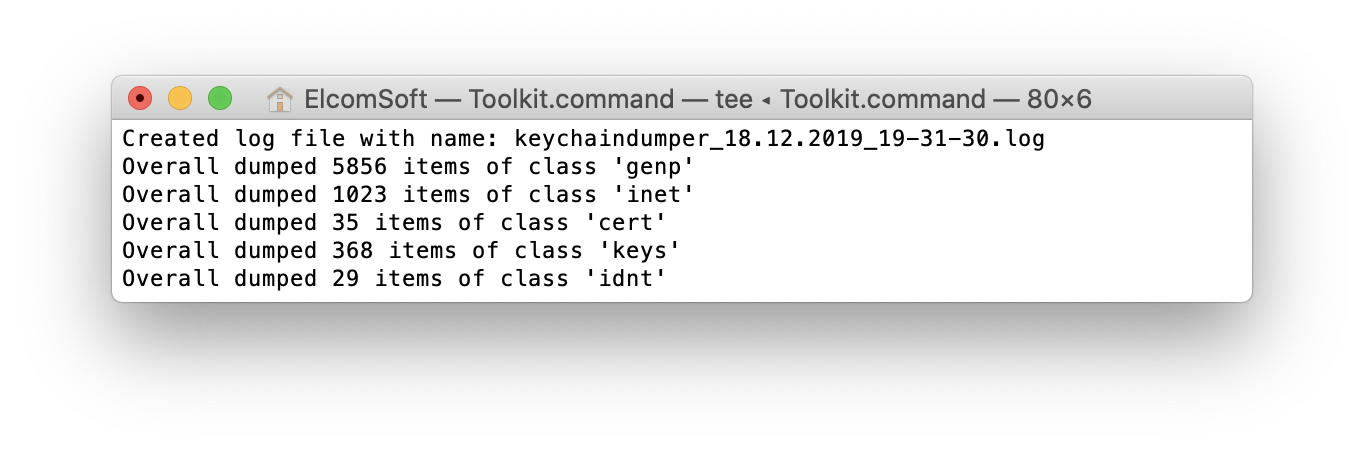
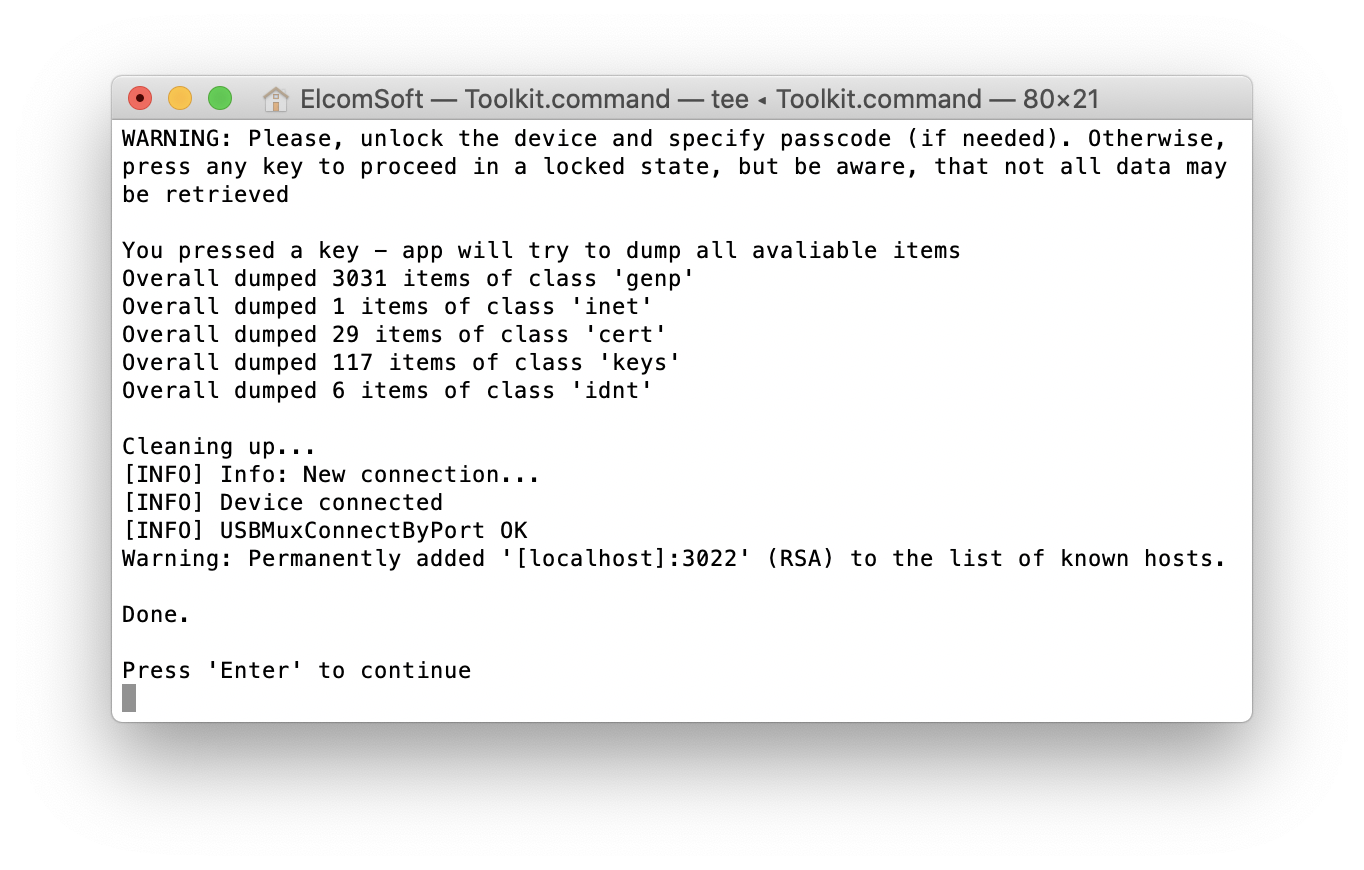 Only records with kSecAttrAccessibleAlways and kSecAttributeAccessibleAlwaysThisDeviceOnly attributes will be extracted (for more information on keychain protection classes and what particular records are available in BFU mode, see Keychain data class protections in Apple Platform Security (Fall 2019). There can be a lot of those, as you can see in the screen shot. Of course, there would be a lot more records available in the AFU mode (including all passwords saved on the device, authentication tokens, decryption keys for secure messengers such as Signal and WhatsApp, etc.):
Only records with kSecAttrAccessibleAlways and kSecAttributeAccessibleAlwaysThisDeviceOnly attributes will be extracted (for more information on keychain protection classes and what particular records are available in BFU mode, see Keychain data class protections in Apple Platform Security (Fall 2019). There can be a lot of those, as you can see in the screen shot. Of course, there would be a lot more records available in the AFU mode (including all passwords saved on the device, authentication tokens, decryption keys for secure messengers such as Signal and WhatsApp, etc.):
The keychain is saved as a keychain_UDID_timestamp.xml (where the UDID is the unique ID of the device, and the timestamp is the date and time of the extraction).
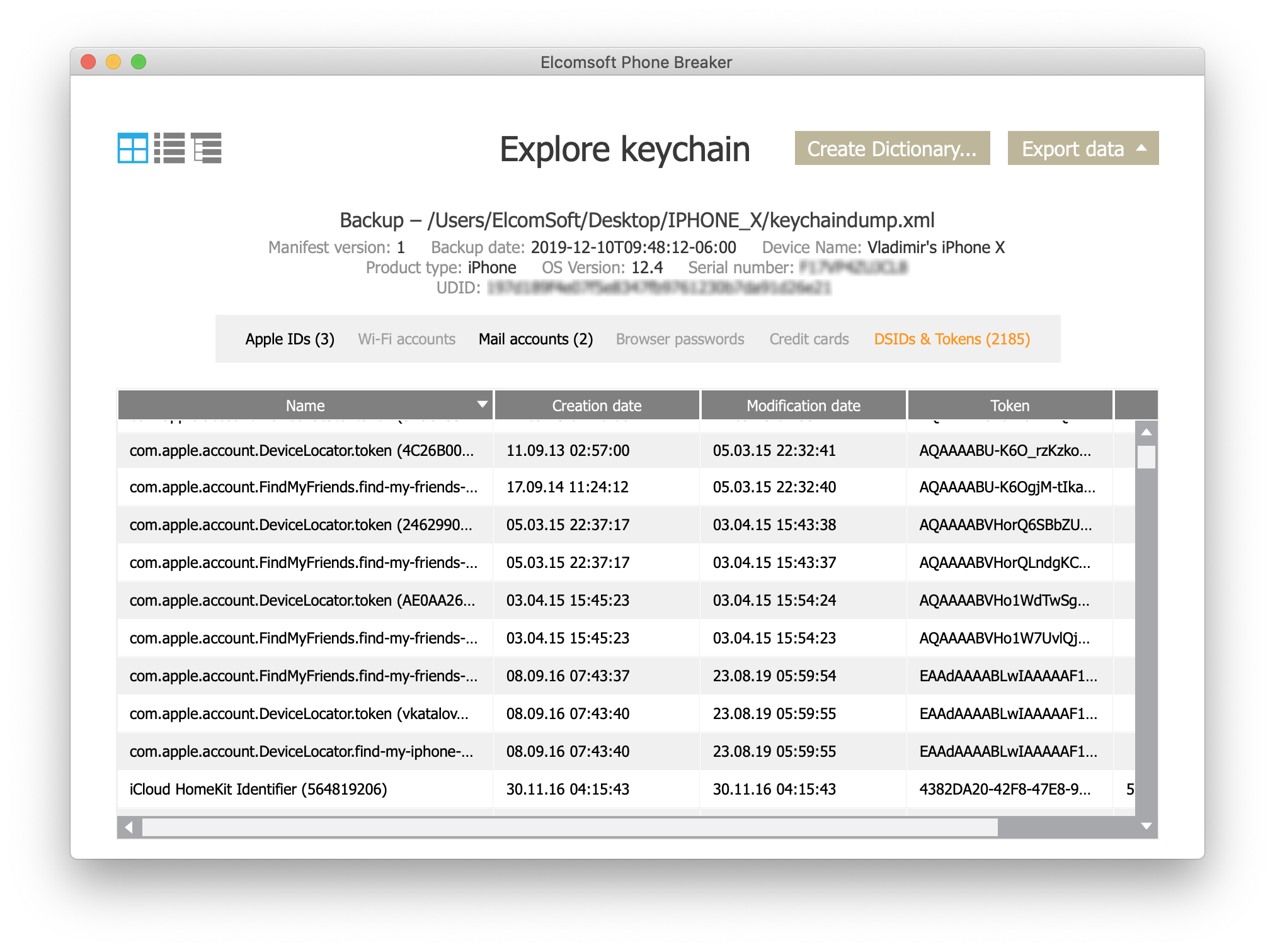
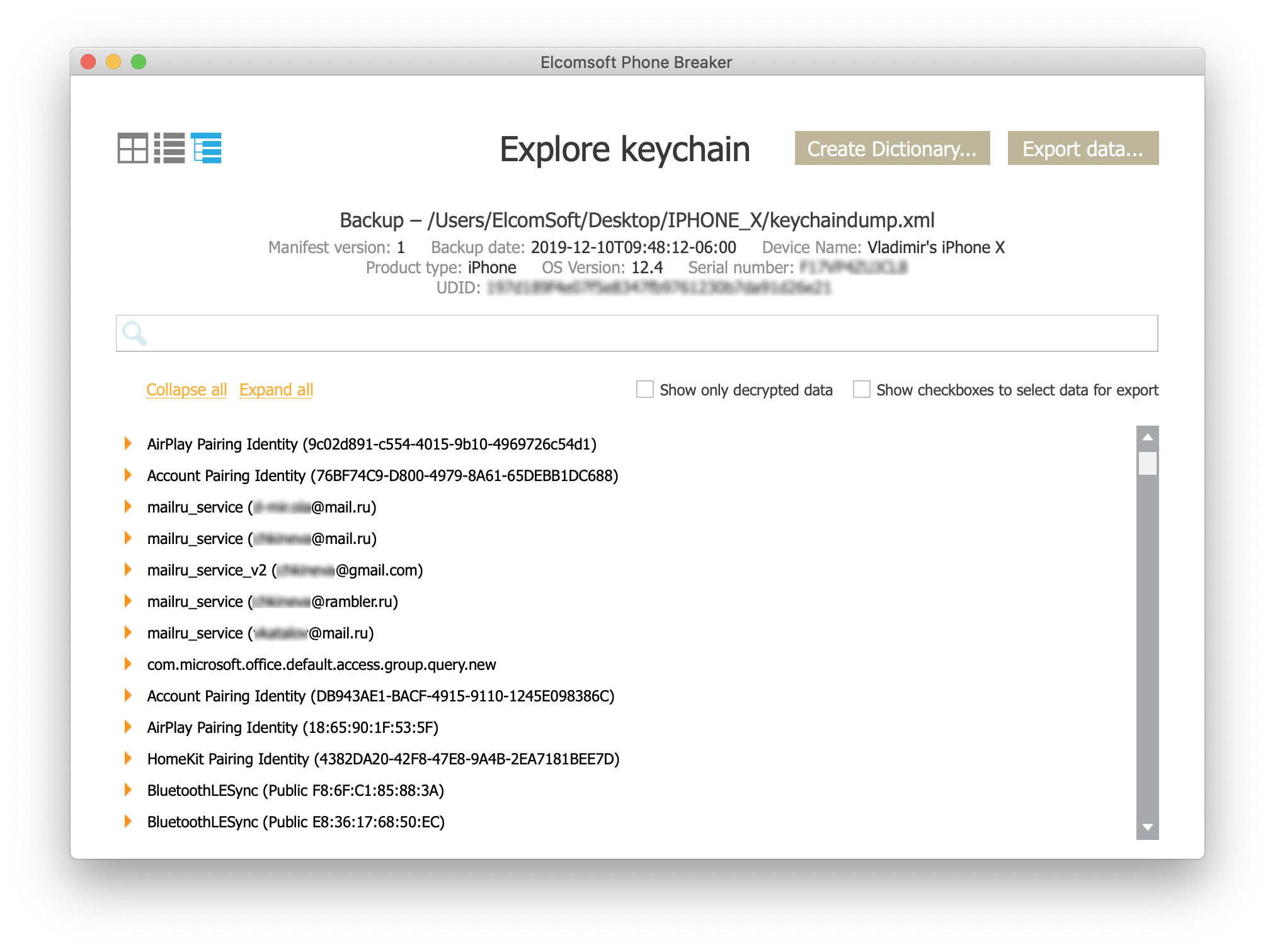
What can you extract, exactly, from locked and disabled devices? You can analyse the extracted keychain manually (as it is in the XML format), but we suggest using Elcomsoft Phone Breaker to explore the keychain (just make sure to rename the file to keychaindump.xml first):
Interestingly, when analyzing my own device, I discovered passwords to mail.ru and rambler.ru accounts, the two popular mail services in Russia. The location was a bit unusual:
I have no idea where they come from, probably leaked from some insecure apps.
Anything else? Some keychain records contain account names (typically email addresses), as well as the user’s Skype account ID.
DFU and USB Restricted Mode
Not to be confused with BFU (Before First Unlock), the DFU mode stands for “Device Firmware Upgrade”. The checkra1n jailbreak utilizes the DFU mode for installation. When I performed the initial tests jailbreaking an iOS 13.3 device, I discovered that the device enters the USB restricted mode on reboot after installing the checkra1n. Our initial reaction was to blame (or praise) Apple for attempting to patch the jailbreak. I was wrong; the problem was in the jailbreak itself. The last two versions (0.9.7 and 0.9.6) are the ones affected. Instead, use a specific version of checkra1n 0.9.5 (https://checkra.in/releases/); it works just as well even with devices where the USB restricted mode is already activated. The only problem is that 0.9.5 does not support certain devices.
For more information on USB restricted mode, see Activating data connections securely in the same Apple Platform Security (Fall 2019) mentioned above (direct link to full PDF document):
To improve security while maintaining usability Touch ID, Face ID, or passcode entry is required to activate data connections via the Lightning, USB, or Smart Connector interface if no data connection has been established recently. This limits the attack surface against physically connected devices such as malicious chargers while still enabling usage of other accessories within reasonable time constraints. If more than an hour has passed since the iOS or iPadOS device has locked or since an accessoryʼs data connection has been terminated, the device wonʼt allow any new data connections to be established until the device is unlocked. During this hour period, only data connections from accessories that have been previously connected to the device while in an unlocked state will be allowed. These accessories are remembered for 30 days after the last time they were connected. Attempts by an unknown accessory to open a data connection during this period will disable all accessory data connections over Lighting, USB, and Smart Connector until the device is unlocked again. This hour period:
- Ensures that frequent users of connections to a Mac or PC, to accessories, or wired to CarPlay wonʼt need to input their passcodes every time they attach their device.
- Is necessary because the accessory ecosystem doesnʼt provide a cryptographically reliable way to identify accessories before establishing a data connection.
In addition, if itʼs been more than three days since a data connection has been established with an accessory, the device will disallow new data connections immediately after it locks. This is to increase protection for users that donʼt often make use of such accessories. Data connections over Lightning, USB, and Smart Connector are also disabled whenever the device is in a state where it requires a passcode to reenable biometric authentication.
The user can choose to reenable always-on data connections in Settings (setting up some assistive devices does this automatically).
The Analysis
Elcomsoft Phone Breaker can be used to analyse the contents of the keychain, but what about the full system image? The file system is acquired with the UDID_timestamp.tar name (instead of user.tar in older versions of iOS Forensic Toolkit). We recommend using Elcomsoft Phone Viewer (Forensic edition), a very simple and lightning fast tool that displays a number of data categories:
In the BFU mode (unknown device passcode), you can get the list of installed applications, some Wallet data (that was a surprise, I have no idea why they are not encrypted), the list of Wi-Fi connections, a lot of media files, notifications (these may contain some chat messages and other useful data). There are also a lot of location points.
Alternatively, you can use third-party forensic software. We evaluated most tools available on the market, and can recommend Oxygen Forensic Detective, which we find to be the best in its class. Oxygen makes a fast, convenient and full-featured toolkit (and analyses a lot of system data well hidden in the system); far way better than the dramatically expensive and slow Cellebrite UFED Physical Analyzer that used to be the leader in the past. In our experience, Oxygen delivers the most comprehensive analysis of the complete TAR images captured by iOS Forensic Toolkit, including the knowledgeC.db database everyone is raving about. Oxygens were quick to support BFU dumps as well, processing files such as /private/var/wireless/Library/Databases/DataUsage.sqlite (apps’ network activities), /private/var/preferences/ (network interfaces) or /private/var/mobile/Library/Voicemail/ (voicemail messages). While many forensic tools analyze those files, it was Oxygen Forensic Detective that returned the largest true number of artifacts.
Yes, all this data is from BFU extraction. Pay attention to the “Image Categorization” – this the new built-in feature introduced in latest Oxygen Forensic Detective, that allows to detect, analyze, and categorize images from twelve different categories, such as weapon, drugs, child abuse, extremism and more.
Finally, you can unpack the .tar archive and analyse the data manually; please refer to Analyzing extractions “Before First Unlock” for additional information, locations of interesting data available in BFU state and more analysis tips.
BFU extraction of the file system provides only a limited set of data. For example, my favorite test device (iPhone X running iOS 12.4) is packed with about 150 GB of data. The BFU acquisition of that device can only access 45 GB of that data.
More Information
We have additional information in The Art of iPhone Acquisition. Shall you need hands-on experience, we are offering a range of trainings on both mobile and desktop forensics.
Future Work
We will continue working on integrating the checkra1n jailbreak and the underlying checkm8 exploit with our tool. iOS acquisition through jailbreaking is often the only method to get the data, but at this point it’s not nearly forensically sound as it alters the content of the file system. Many things installed by the jailbreak are not needed for the extraction. In addition, jailbreaking is still a bit risky. However, we are working on integrating the low-level checkm8 exploit into our software. This should straighten up the process, making it faster, simpler, safer and completely forensically sound.