This post continues the series of articles about Apple companion devices. If you haven’t seen them, you may want to read Apple TV and Apple Watch Forensics 01: Acquisition first. If you are into Apple Watch forensics, have a look at Apple Watch Forensics 02: Analysis as well. Today we’ll have a look at what’s inside of the Apple TV.
A recent market analysis shows that Apple has sold more than 13 million Apple TV devices worldwide since 2016. Since 2007, Apple manufactured 6 different Apple TV models. Like any other Apple device, the model can be easily identified by checking the label on the bottom of the device.
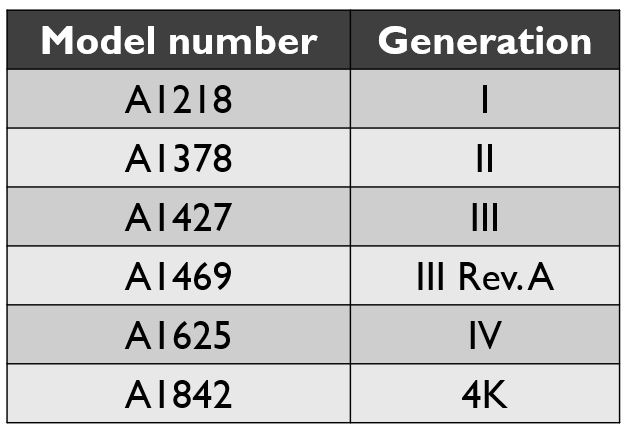

The first-generation Apple TV (model A1218) contains a regular hard drive that can be extracted and imaged with a traditional approach. The operating system is a modified version of Mac OS X 10.4 (Tiger). A detailed explanation on how to approach this kind of devices was introduced at DEFCON 2009 by Kevin Estis and Randy Robbins (the presentation is available here while the video is available here).
The Apple TV from second (model A1378) to fourth (A1625) generations have an internal NAND storage varying from 8 GB (A1378 – A1427 – A1469) to 32 or 64 GB (A1625). These models also feature a USB port connection (micro USB or USB-C). The availability of a USB port allows connecting the device to a PC/Mac. Forensic experts can use the port for data extraction. Apple removed USB connectivity in the latest, fifth generation Apple TV (Apple TV 4K, model A1842), making it more difficult to connect and extract data.
The good news from a forensic perspective is that these kind of devices cannot be protected with a passcode, unlike the iPhone, iPad or Apple Watch. The bad news is that the backup service available on the iPhone and on the iPad is missing on the Apple TV. The USB port is meant to be a “Service and Support” port. Its intended purpose is to restore or update the operating system through the computer. By simply connecting the Apple TV to a computer with iTunes installed, one can access information such as the serial number and the UDID of the device. As described in previous blog post on Apple TV Acquisition, three methods of acquisition are always available:
- Device information (the “I” option in Elcomsoft iOS Forensic Toolkit)
- Device name
- Model number
- Serial number
- Operating system version
- UDID
- Wi-Fi MAC Address
- Ethernet MAC address
- Bluetooth MAC address
- Date and time
- Timezone
- Language
- Data partition information (size, disk usage, available space)
- Detailed list of installed application (bundle name, bundle version)
- AFC Protocol (Apple File Conduit) (the “M” option in Elcomsoft iOS Forensic Toolkit)
- DCIM folder, possibly containing photos synced through iCloud
- Thumbnails folder, possibly containing thumbnails of photo synced through iCloud
- MediaLibrary.sqlitedb, containing the user iCloud account ID and the shopping database on the iTunes Store
- Photos.sqlite, a database containing information about images
- Logs (the “L” option in Elcomsoft iOS Forensic Toolkit)
- Sysdiagnose log, that can be generated on the Apple TV 4 and 4K by following the instruction available on Apple Developer website (login is required, but no Apple Developer account is required)
- Crash Logs, possibly containing information about application usage
- Wi-Fi Logs, containing information about Wi-Fi network the Apple TV was connected to
For a detailed explanation on how to analyze these files you can read my previous blog post on Apple Watch Analysis: the structure of databases (MediaLibrary.sqlitedb and Photos.sqlite) and Sysdiagnose logs is coherent among those devices. Moreover, real-time syslog can be extracted from any Apple TV model by using e.g. the iBackup Bot tool , or with Apple XCode.
The Apple TV 4K (model A1842) does not feature a USB port, so the direct connection is not possible. You may connect through Wi-Fi with a Mac. The generation of sysdiagnose data is also available on the Apple TV 4K; it can be synced with macOS through XCode. Although not completely documented by Apple, some information is available here on the Apple Forum Developer website (restricted access).
As described in the Apple TV acquisition article, jailbreaking the device is an option available for different versions of tvOS, the Apple TV operating system. You can find here the detailed list of available jailbreaks for the Apple TV. Once you have a jailbroken device, you have access to the file system. Below is the list of some of the most interesting information you can find.
System information
Network TCP/IP lease
Path: /private/var/DB/DHCPCLIENT/LEASES/
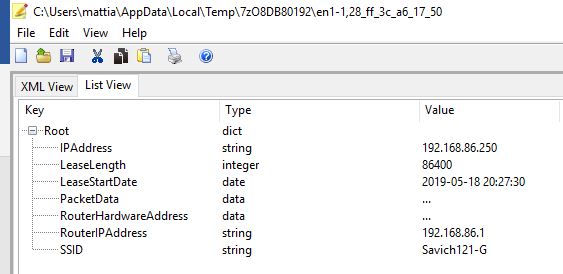
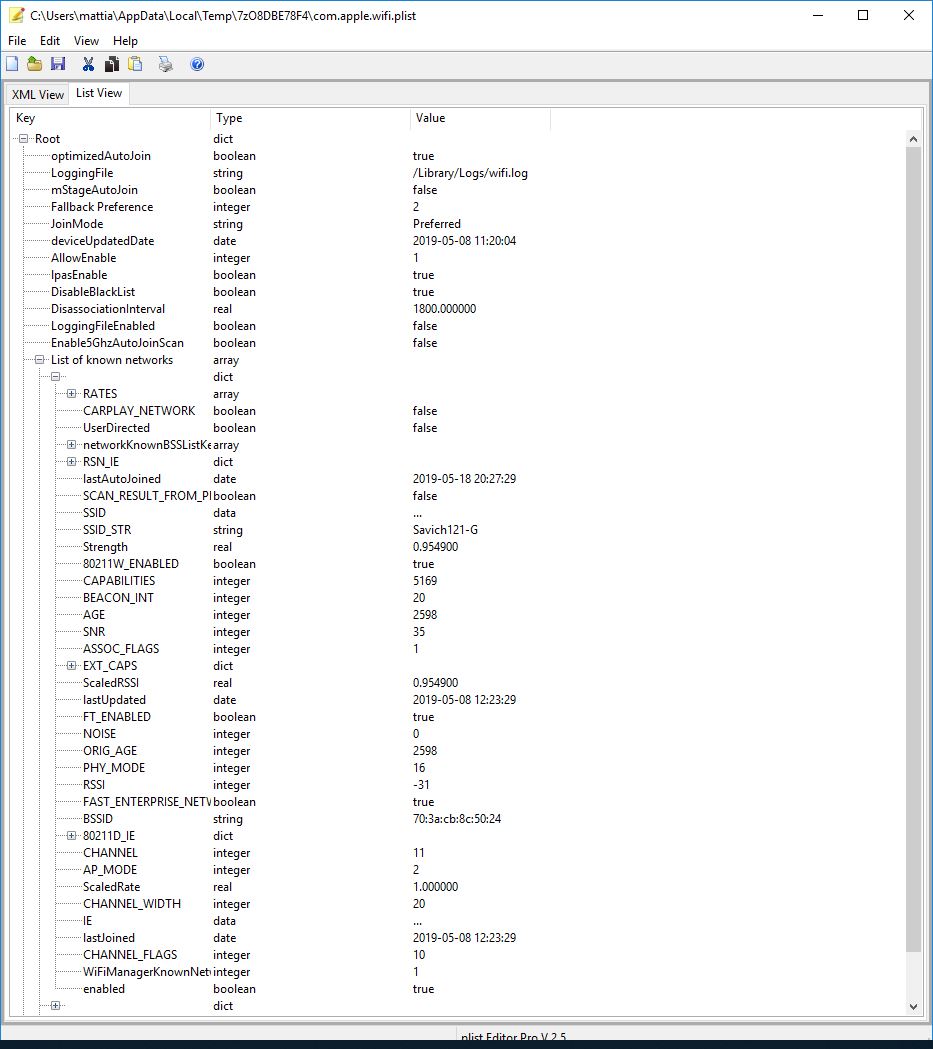
Network Wi-Fi History
Path: /private/var/preferences/SystemConfiguration/com.apple.wifi.plist
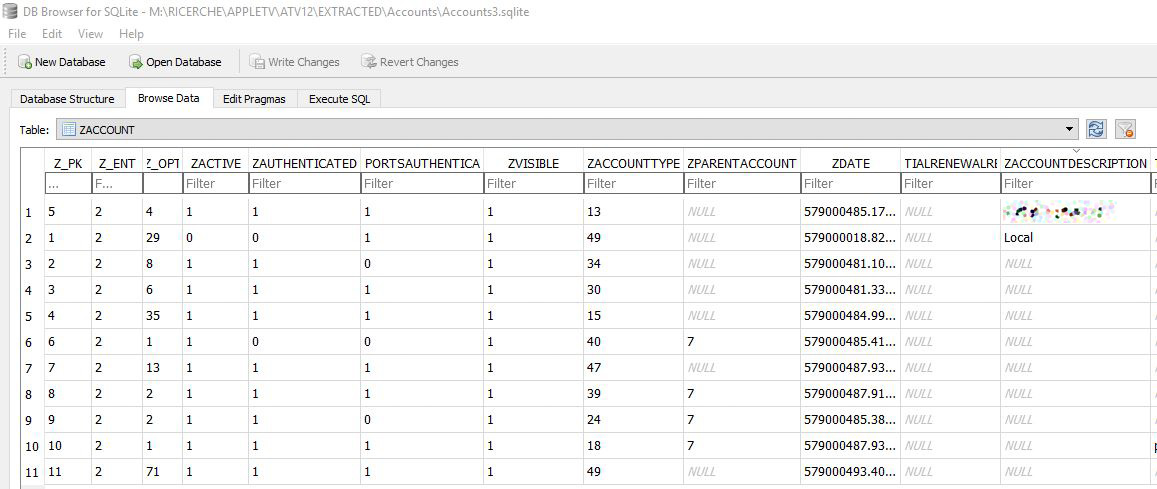
Accounts
Path: /private/var/mobile/Library/Accounts/Accounts3.sqlite
Usage information
HeadBoard
Path: /private/var/mobile/Library/com.apple.HeadBoard/
This folder lists the app order on the Head Board (AppOrder.plist) and contains the associated Icons Cache (subfolder com.apple.TVIconsCache)

The HeadBoard cache is stored in /private/var/mobile/Library/Caches/com.apple.HeadBoard
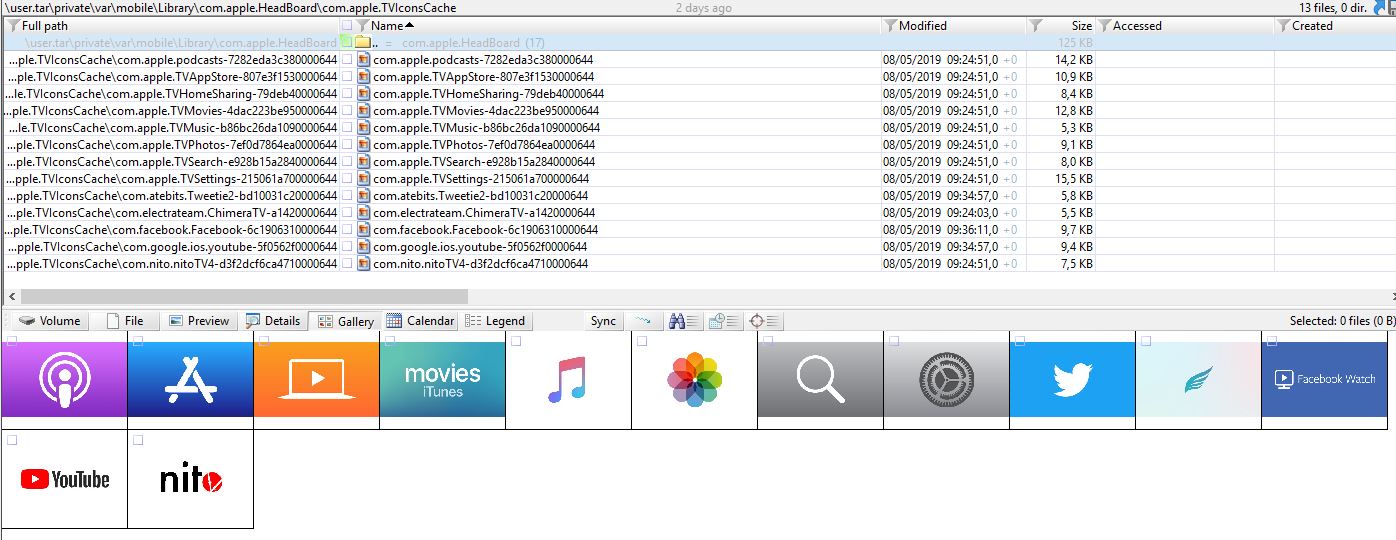
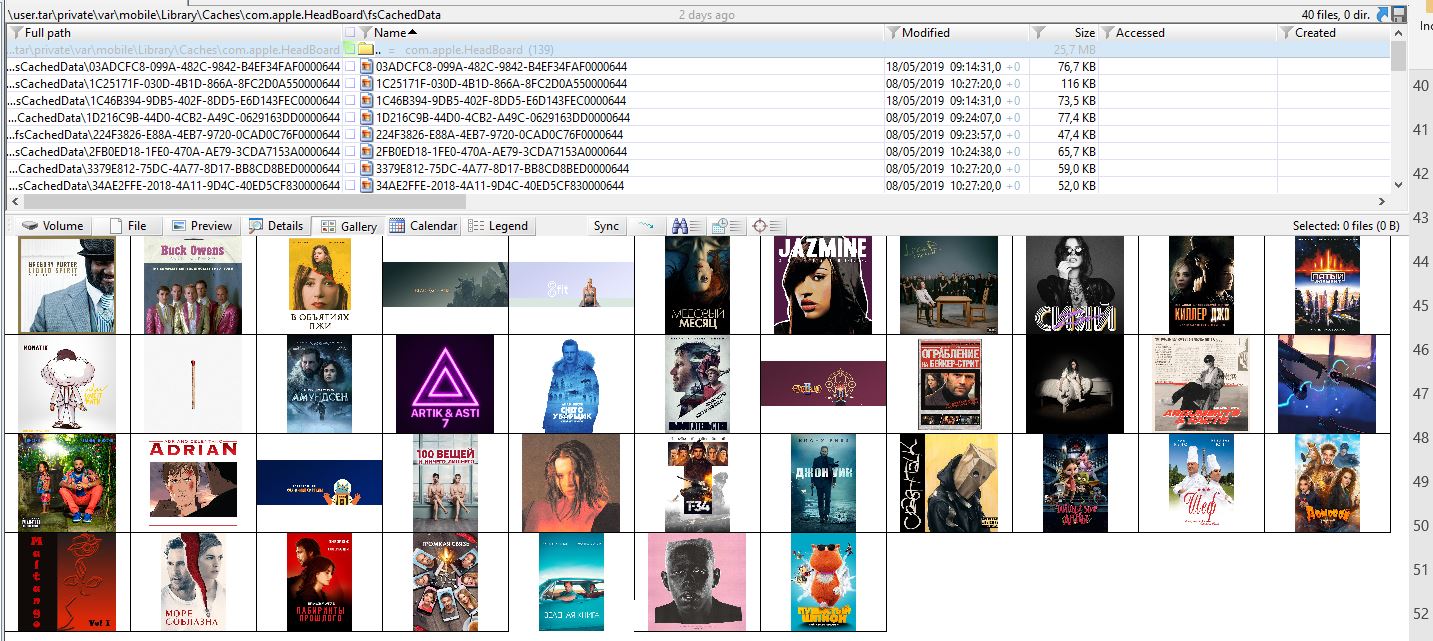
TVWallpaper
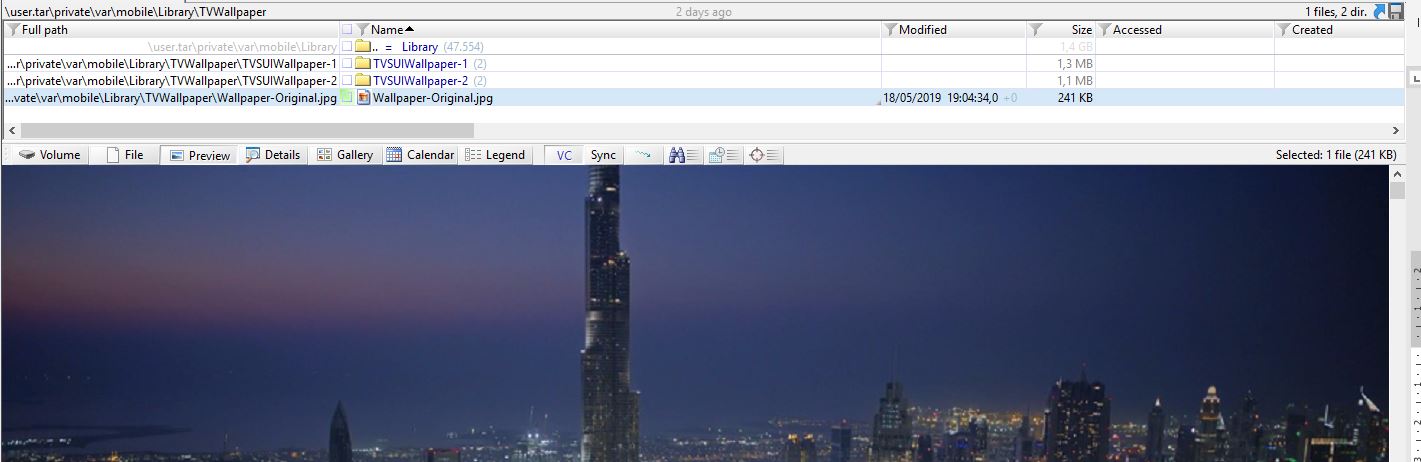
Path: /private/var/mobile/Library/TVWallpaper/
The folder contains Apple TV wallpapers
Other relevant files and folders you can find are:
- Preferences folder (path: /private/var/mobile/Library/Preferences/), containing various preferences file in plist format
- Synced Preferences folder (path: /private/var/mobile/Library/SyncedPreferences/), containing various preferences file in plist format synced from other devices associated with the same iCloud account. The most relevant files are apple.wifid.plist (Wi-Fi networks) and com.apple.nanoweatherprefsd.plist (Weather information)
- Mobile Installation Logs folder (path: /private/var/mobile/Library/MobileInstallation/), containing information about installed apps. They can be parsed with “Mobile Installation Logs Parser” by Alexis Brignoni. This folder is also available in sysdiagnose acquisition.
- Mobile Activation Logs folder (path: /private/var/mobile/Library/Logs/mobileactivationd/), containing information about Mobile Activation and operating system upgrades. They can be parsed with “Mobile Activation” script by Cheeky4n6monkey. This folder is also available in sysdiagnose acquisition.
- Mobile Container Manager Logs folder (path: /private/var/mobile/Library/MobileContainerManager/ and /private/var/root/Logs/MobileContainerManager/), containing information about Mobile Containers. They can be parsed with “Mobile Container Manager” script by Cheeky4n6monkey. This folder is also available in sysdiagnose acquisition.
- KnowledgeC database (path: /private/var/mobile/Library/CoreDuet/Knowledge/knowledgeC.db)
- NetUsage database (path: /private/var/networkd/netusage.sqlite)
- InteractionC database (path: /private/var/mobile/Library/CoreDuet/People/InteractionC.db)
- Cache_EncryptedB and Cache_EncryptedC databases (path /private/var/root/Library/Caches/locationd/)
Third-Party Applications
Third-party applications can be installed on the Apple TV from the App Store.
Bundles of installed applications are located in /private/var/Containers/Bundle/Application
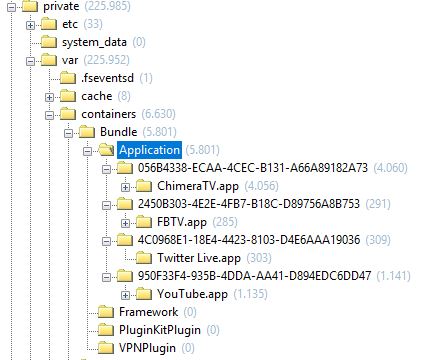
Third-party app data is stored in /private/var/mobile/Containers/Data/Application

Every application has its own folder for storing settings and data. In the following picture you can see the example of the “Facebook TV” application.
Apple TV and Location Data: iCloud Photos, Thumbnails and EXIF
The one thing I’d like to shed some more light on is iCloud Photos. It’s far more important than it may seem. While accessing iCloud Photos from the computer requires the user’s Apple ID and password (and possibly access to the second authentication factor), the Apple TV may have the Thumbnails stored right on the box. This happens automatically if the user is syncing photos with iCloud.
Interestingly, the thumbnails synced to the Apple TV still contain full EXIF information. It is the same metadata that’s stored in full-size photos. The EXIF may (and usually does) contain location information either directly in the photo or in the Photos.sqlite database.
Full images are there if and only if the user opened the image on the Apple TV (that would mean that the image was downloaded).
Apple TV Keychain
In addition to iCloud Photos, Elcomsoft iOS Forensic Toolkit can extract the keychain from jailbroken Apple TV devices. Apple TV keychain is often overlooked. It contains far less information compared to iOS keychain due to the fact that Apple TV does not sync iCloud Keychain (the iCloud Keychain requires the device to have a passcode to sync, which Apple TV devices lack). However, Apple TV keychain still contains Wi-Fi passwords and stores an authentication token to the user’s iCloud account. Extracting that token allows experts accessing non-2FA iCloud accounts with very few restrictions (with Elcomsoft Phone Breaker)..
Acknowledgements
I would like to thank Claudia Meda who helped me a lot with the Apple TV research last year. She regularly tweets about forensic news and events.
Conclusion
If you can extract the file system of an Apple TV 4 or 4K, you gain access to a plethora of data. Quite a few bits and pieces have forensic significance. The analysis of the Apple TV can provide the examiner access to three different sources of information:
- The life and usage of the Apple TV itself;
- Cloud data such as synced images and videos;
- Location data extracted from synced thumbnails (iCloud Photos);
- Preferences synced through iCloud (Wi-Fi networks, Weather and so on).
We consider the Apple TV a “low hanging fruit” as (unlike the iPhone) the device cannot be protected with a passcode. Connecting the latest model (Apple TV 4K) is more difficult due to the lack of a USB port; one must use Xcode to establish a wireless connection.